A) TACACS
B) CPU ACL
C) Flex ACL
D) RADIUS
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which type of authentication and encryption does SNMPv3 use at the authPriv security level?
A) username authentication with MD5 or SHA encryption
B) MD5 or SHA authentication with DES encryption
C) username authentication with DES encryption
D) DES authentication with MD5 or SHA encryption
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which WAN access technology is preferred for a small office / home office architecture?
A) broadband cable access
B) frame-relay packet switching
C) dedicated point-to-point leased line
D) Integrated Services Digital Network switching
Correct Answer

verified
Correct Answer
verified
Multiple Choice
If a notice-level message is sent to a syslog server, which event has occurred?
A) A network device has restarted.
B) A debug operation is running.
C) A routing instance has flapped.
D) An ARP inspection has failed.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An engineer must configure a WLAN using the strongest encryption type for WPA2-PSK. Which cipher fulfills the configuration requirement?
A) WEP
B) AES
C) RC4
D) TKIP
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An office has 8 floors with approximately 30-40 users per floor. One subnet must be used. Which command must be configured on the router Switched Virtual Interface to use address space efficiently?
A) ip address 192.168.0.0 255.255.0.0
B) ip address 192.168.0.0 255.255.254.0
C) ip address 192.168.0.0 255.255.255.128
D) ip address 192.168.0.0 255.255.255.224
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What are two functions of a Layer 2 switch? (Choose two.)
A) acts as a central point for association and authentication servers
B) selects the best route between networks on a WAN
C) moves packets within a VLAN
D) moves packets between different VLANs
E) makes forwarding decisions based on the MAC address of a packet
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which action does the router take as it forwards a packet through the network?
A) The router encapsulates the original packet and then includes a tag that identifies the source router MAC address and transmits it transparently to the destination.
B) The router encapsulates the source and destination IP addresses with the sending router IP address as the source and the neighbor IP address as the destination.
C) The router replaces the original source and destination MAC addresses with the sending router MAC address as the source and neighbor MAC address as the destination.
D) The router replaces the source and destination labels with the sending router interface label as a source and the next hop router label as a destination.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
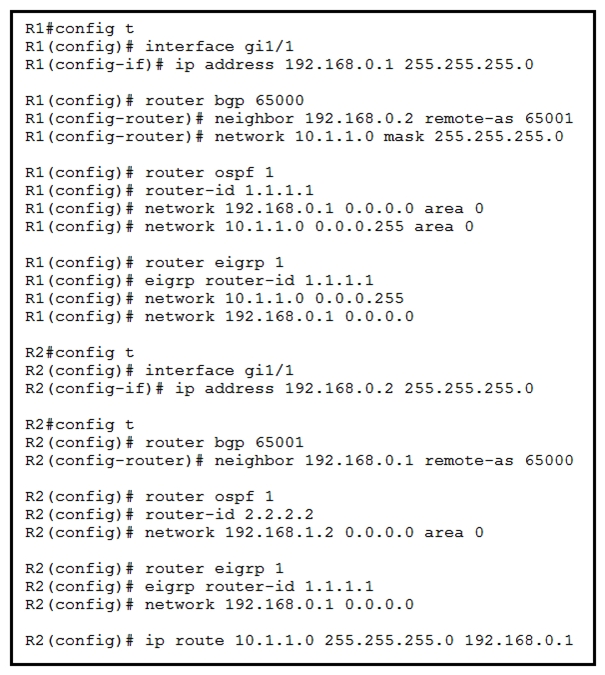 Refer to the exhibit. Router R2 is configured with multiple routes to reach network 10.1.1.0/24 from router R1. Which path is chosen by router R2 to reach the destination network 10.1.1.0/24?
Refer to the exhibit. Router R2 is configured with multiple routes to reach network 10.1.1.0/24 from router R1. Which path is chosen by router R2 to reach the destination network 10.1.1.0/24?
A) static
B) EIGRP
C) eBGP
D) OSPF
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A user configured OSPF in a single area between two routers. A serial interface connecting R1 and R2 is running encapsulation PPP. By default, which OSPF network type is seen on this interface when the user types show ip ospf interface on R1 or R2?
A) nonbroadcast
B) point-to-point
C) point-to-multipoint
D) broadcast
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Refer to the exhibit. The network administrator wants VLAN 67 traffic to be untagged between Switch 1 and Switch 2, while all other VLANs are to remain tagged. Which command accomplishes this task? 
A) switchport access vlan 67
B) switchport trunk allowed vlan 67
C) switchport private-vlan association host 67
D) switchport trunk native vlan 67
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Refer to the exhibit. After you apply the given configurations to R1 and R2 you notice that OSPFv3 fails to start. 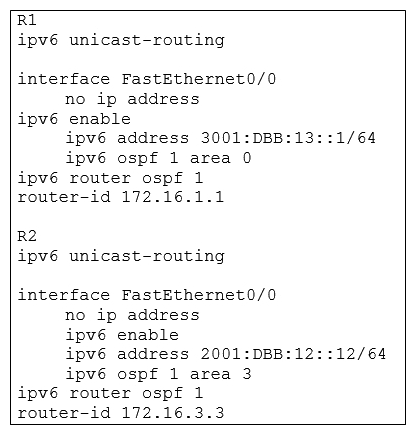
A) The area numbers on R1 and R2 are mismatched
B) The IPv6 network addresses on R1 and R2 are mismatched
C) The autonomous system numbers on R1 and R2 are mismatched
D) The router ids on R1 and R2 are mismatched
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A manager asks a network engineer to advise which cloud service models are used so employees do not have to waste their time installing, managing, and updating software that is only used occasionally. Which cloud service model does the engineer recommend?
A) infrastructure-as-a-service
B) platform-as-a-service
C) business process as service to support different types of service
D) software-as-a-service
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which statement correctly compares traditional networks and controller-based networks?
A) Only controller-based networks decouple the control plane and the data plane.
B) Traditional and controller-based networks abstract policies from device configurations.
C) Only traditional networks natively support centralized management.
D) Only traditional networks offer a centralized control plane.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What are two descriptions of three-tier network topologies? (Choose two.)
A) The distribution layer runs Layer 2 and Layer 3 technologies
B) The network core is designed to maintain continuous connectivity when devices fail
C) The access layer manages routing between devices in different domains
D) The core layer maintains wired connections for each host
E) The core and distribution layers perform the same functions
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The OSPF Hello protocol performs which of the following tasks? (Choose two.)
A) It provides dynamic neighbor discovery.
B) It detects unreachable neighbors in 90 second intervals.
C) It maintains neighbor relationships.
D) It negotiates correctness parameters between neighboring interfaces.
E) It uses timers to elect the router with the fastest links as the designated router.
F) It broadcasts hello packets throughout the internetwork to discover all routers that are running OSPF.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
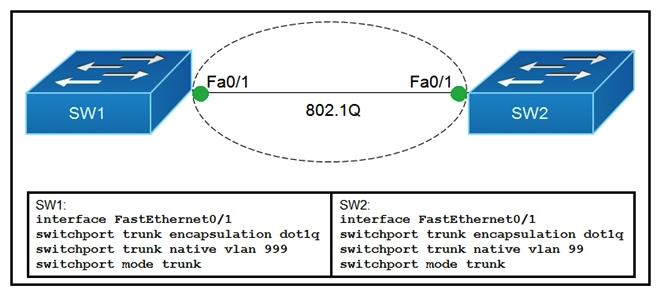 Refer to the exhibit. Which action do the switches take on the trunk link?
Refer to the exhibit. Which action do the switches take on the trunk link?
A) The trunk does not form, and the ports go into an err-disabled status.
B) The trunk forms, but the mismatched native VLANs are merged into a single broadcast domain.
C) The trunk forms, but VLAN 99 and VLAN 999 are in a shutdown state.
D) The trunk does not form, but VLAN 99 and VLAN 999 are allowed to traverse the link.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What benefit does controller-based networking provide versus traditional networking?
A) allows configuration and monitoring of the network from one centralized point
B) provides an added layer of security to protect from DDoS attacks
C) combines control and data plane functionality on a single device to minimize latency
D) moves from a two-tier to a three-tier network architecture to provide maximum redundancy
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Refer to the exhibit. C-router is to be used as a "router-on-a-stick" to route between the VLANs. All the interfaces have been properly configured and IP routing is operational. The hosts in the VLANs have been configured with the appropriate default gateway. What is true about this configuration? 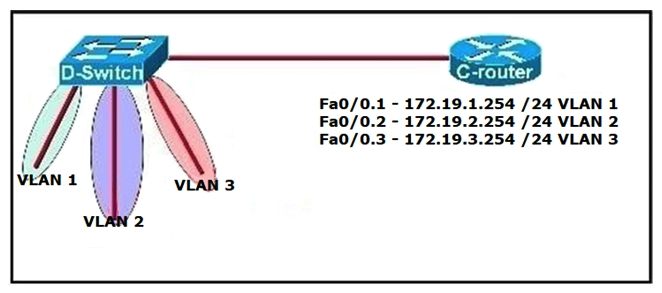
A) These commands need to be added to the configuration: C-router(config) # router eigrp 123 C-router(config-router) # network 172.19.0.0
B) C-router(config) # router ospf 1 C-router(config-router) # network 172.19.0.0 0.0.3.255 area 0
C) C-router(config) # router rip
D) No further routing configuration is required.
Correct Answer

verified
Correct Answer
verified
Multiple Choice
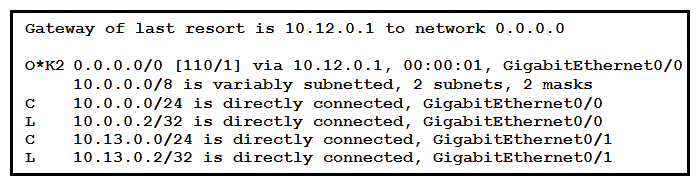 Refer to the exhibit. If configuring a static default route on the router with the ip route 0.0.0.0 0.0.0.0 10.13.0.1 120 command, how does the router respond?
Refer to the exhibit. If configuring a static default route on the router with the ip route 0.0.0.0 0.0.0.0 10.13.0.1 120 command, how does the router respond?
A) It starts sending traffic without a specific matching entry in the routing table to GigabitEthernet0/1.
B) It immediately replaces the existing OSPF route in the routing table with the newly configured static route.
C) It starts load-balancing traffic between the two default routes.
D) It ignores the new static route until the existing OSPF default route is removed.
Correct Answer

verified
Correct Answer
verified
Showing 101 - 120 of 411
Related Exams